Bringing harmony to home container management with Portainer
Getting a handle on the home server sprawl
If you're anything like me, your home network has evolved
How a cybercriminal group is targeting recruiters with malware
Recruiters are always looking for the best talent to fill their vacancies. But what if some candidates who apply for
What is Credential Stuffing and How to Protect Yourself
Credential stuffing is a type of cyberattack that exploits the reuse of usernames and passwords across different websites and applications.
Log4j The pain persists
The log4j vulnerability, also known as Log4Shell, is a serious flaw in a widely used Java logging library that allows
LogoFAIL Vulnerabilities
Critical bugs allow attackers to bypass Secure Boot and install persistent firmware bootkits on devices. They exploit the image-parsing libraries
How I use Cloudflare Zero Trust - Tunnels - to host this blog
Cloudflare tunnels are a secure and convenient way to connect your web applications to Cloudflare’s network without exposing them
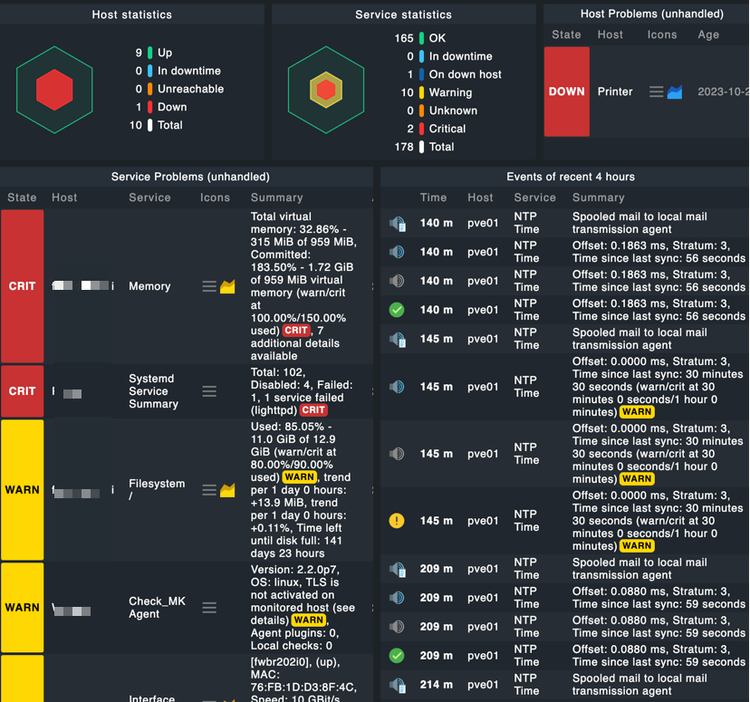
Why I chose Checkmk as my monitoring platform?
Checkmk is a comprehensive platform for monitoring applications, servers, and networks, whether on-premises or in the cloud. It is equipped
Some notes about Google Workspaces Exploits
Researchers have found several ways to exploit Google Workspace and Google Cloud Platform features to conduct ransomware, data exfiltration, and
Mirai - botnet
A new Mirai-based botnet exploits a zero-day vulnerability in thousands of routers and cameras from various brands. The vulnerability allows
SSHFS: A Small Guide for Ubuntu Users
SSHFS, or Secure Shell Filesystem, is a powerful tool that uses SSH to enable the mounting of a remote filesystem